What is Microsoft Defender for Cloud?
Imagine you and your friends are organizing a fun event together. Each person has a specific role to make the event a success. Well, the same idea applies to cloud security — it’s a team effort!
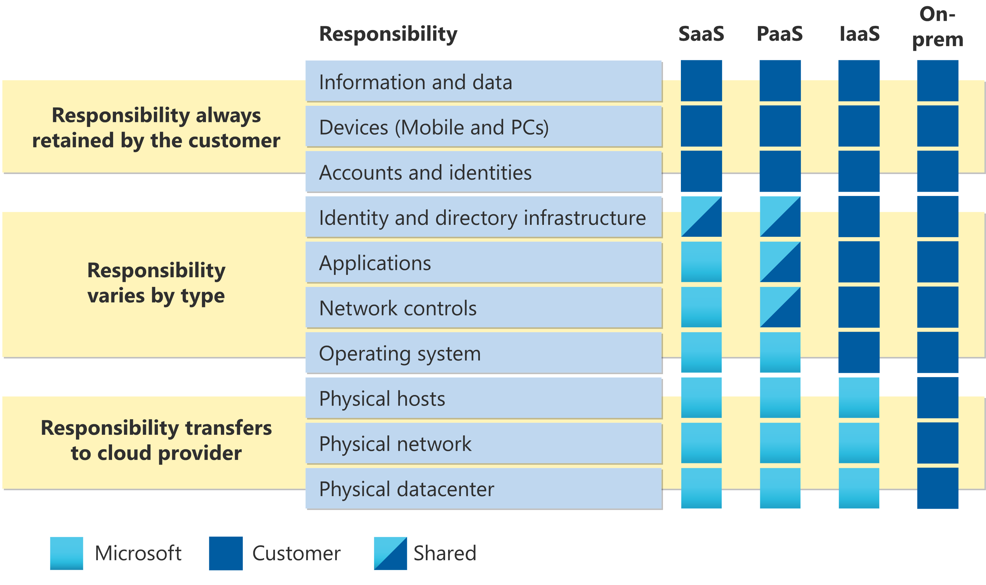
In the world of cloud computing, we have something called the shared responsibility model. It means that both the cloud provider (the folks who give us the cloud services) and the cloud customer (that’s us!) have important responsibilities when it comes to keeping things secure.
Here’s the breakdown:
The cloud provider takes care of securing the physical infrastructure, like the data centers and networks. They have fancy security measures in place to protect against physical and network threats. They also make sure that the cloud services they offer are always available and reliable for us to use.
Now, our part as the cloud customers is to take care of the security of our own stuff. That means things like our applications, data, user access, and configurations. We have to set up strong passwords, control who can access our stuff, and make sure our data is safe by encrypting it. It’s like locking our own rooms to keep our things secure.
By working together, the cloud provider and us—the cloud customers—we create a strong shield of security for our cloud environment. We need to communicate and collaborate with the cloud provider to make sure we understand each other’s responsibilities and cover all the bases. Just like a successful team project, cloud security is about teamwork and everyone doing their part. By understanding our roles and working together, we can keep our cloud-based stuff safe and sound.
Potential Risks with Cloud Services
Sure, the cloud is cool and all, but it’s not perfect. There are potential risks that we need to be aware of to better protect ourselves. Here are some common ones:
- Data Breaches: Sensitive data stored in the cloud gets accessed or exposed without permission.
- Unauthorized Access: Bad actors manage to get into cloud resources, applications, or data without permission.
- Account Hijacking: Someone steals your cloud account details and uses them to control your stuff.
- Insecure Interfaces and APIs: Weak points in cloud interfaces and APIs that attackers can take advantage of.
- Insufficient Data Protection: Data isn’t properly protected with encryption or access controls.
- Insider Threats: Authorized users misuse their privileges or access sensitive data without permission.
- Compliance Challenges: Meeting all the rules and regulations related to data protection and privacy.
Understanding Cloud Security
Let’s take a moment to understand what cloud security is all about. Imagine you have a valuable collection of items that you want to protect—like precious jewels or important documents. In the digital world, cloud security is like a shield that keeps your valuable digital assets safe.
Cloud security involves a set of measures and practices designed to protect your data, applications, and infrastructure in the cloud. It focuses on achieving a few important goals:
- Confidentiality: Ensuring that your sensitive information remains private and accessible only to authorized individuals.
- Integrity: Making sure your data remains accurate and trustworthy, without getting tampered with or altered.
- Availability: Ensuring that your data and services are always accessible when you need them.
- Compliance: Following rules and regulations related to data protection and privacy.
By focusing on these goals, cloud security provides you with peace of mind, knowing that your digital assets are protected. Now, let’s dive into one of the key tools in the cloud security arsenal — Microsoft Defender for Cloud.
Introducing Microsoft Defender for Cloud

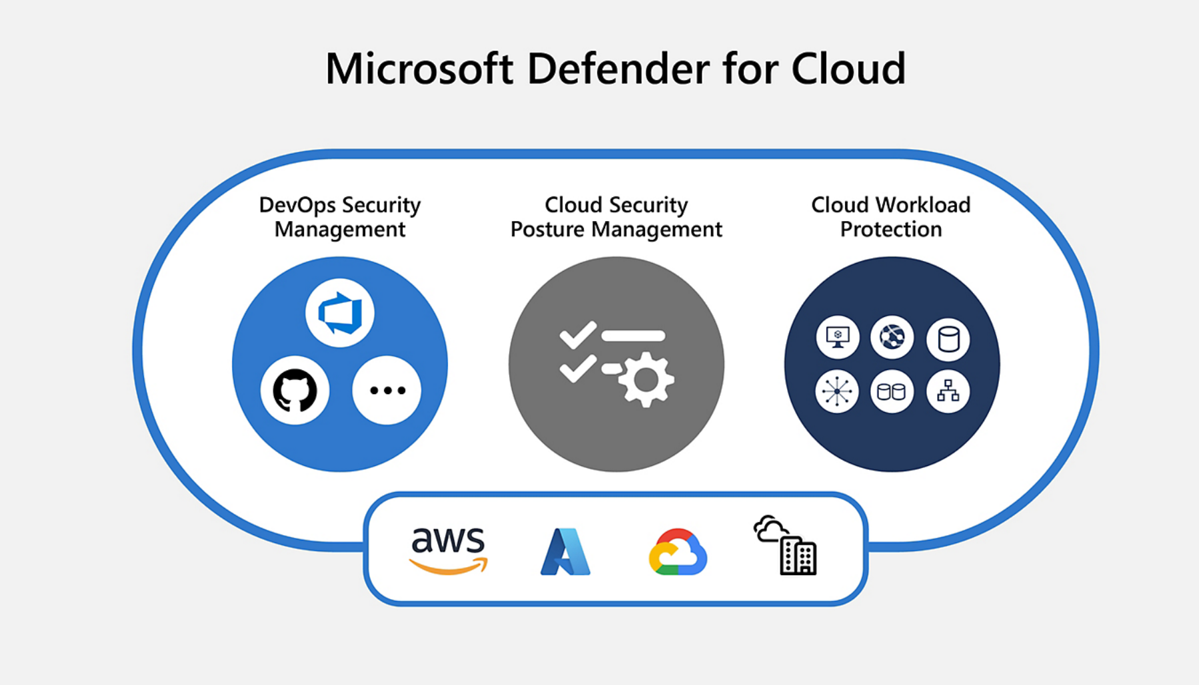
Microsoft Defender for Cloud is a cloud security solution that helps you protect your Azure resources from a wide range of threats. It provides a comprehensive set of features, including:
- Cloud Security Posture Management (CSPM): Helps you identify and remediate security misconfigurations in your Azure resources.
- Cloud Workload Protection (CWPP): Provides real-time protection for your Azure workloads from malware, ransomware, and other threats.
- Threat Protection: Monitors your Azure resources for threats and provides alerts and recommendations.
- Incident Response: Helps you investigate and respond to security incidents in your Azure resources.
Key Features of Microsoft Defender for Cloud
Let’s delve deeper into some of the key features of Microsoft Defender for Cloud:
Cloud Security Posture Management (CSPM)
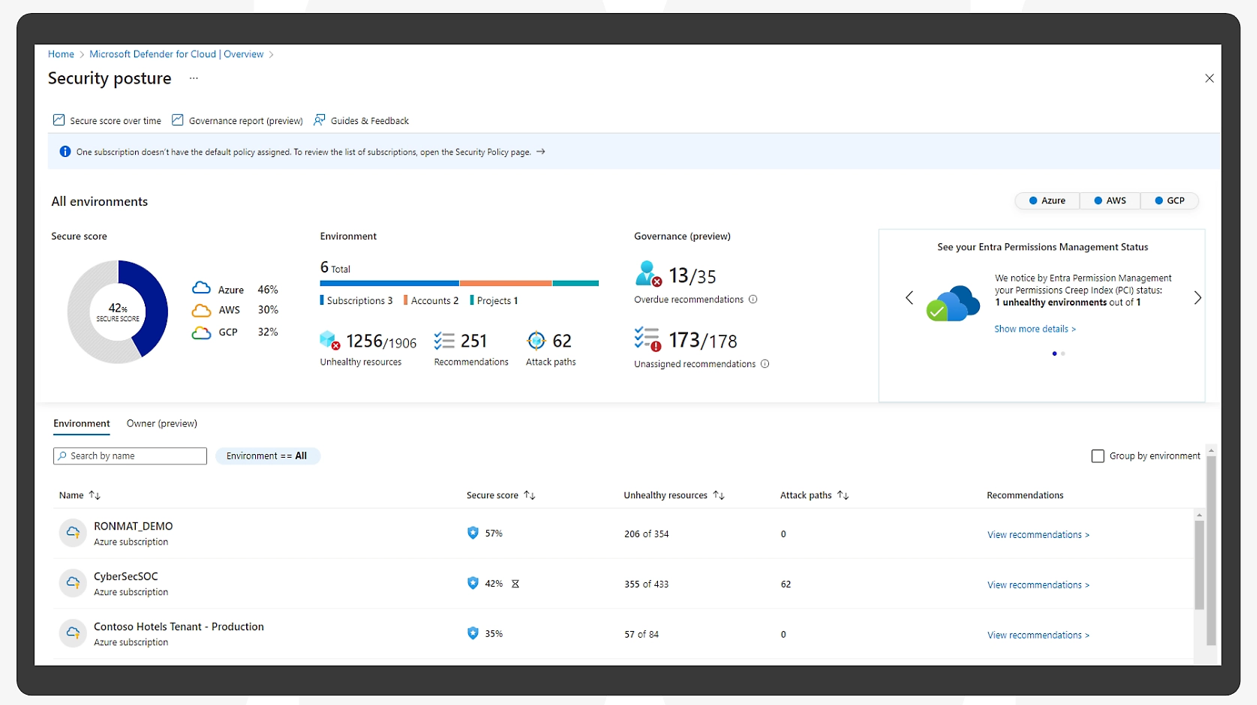
CSPM helps you identify and remediate security misconfigurations in your Azure resources. It scans your Azure resources for known security misconfigurations and provides recommendations for how to fix them.
Cloud Workload Protection (CWPP)
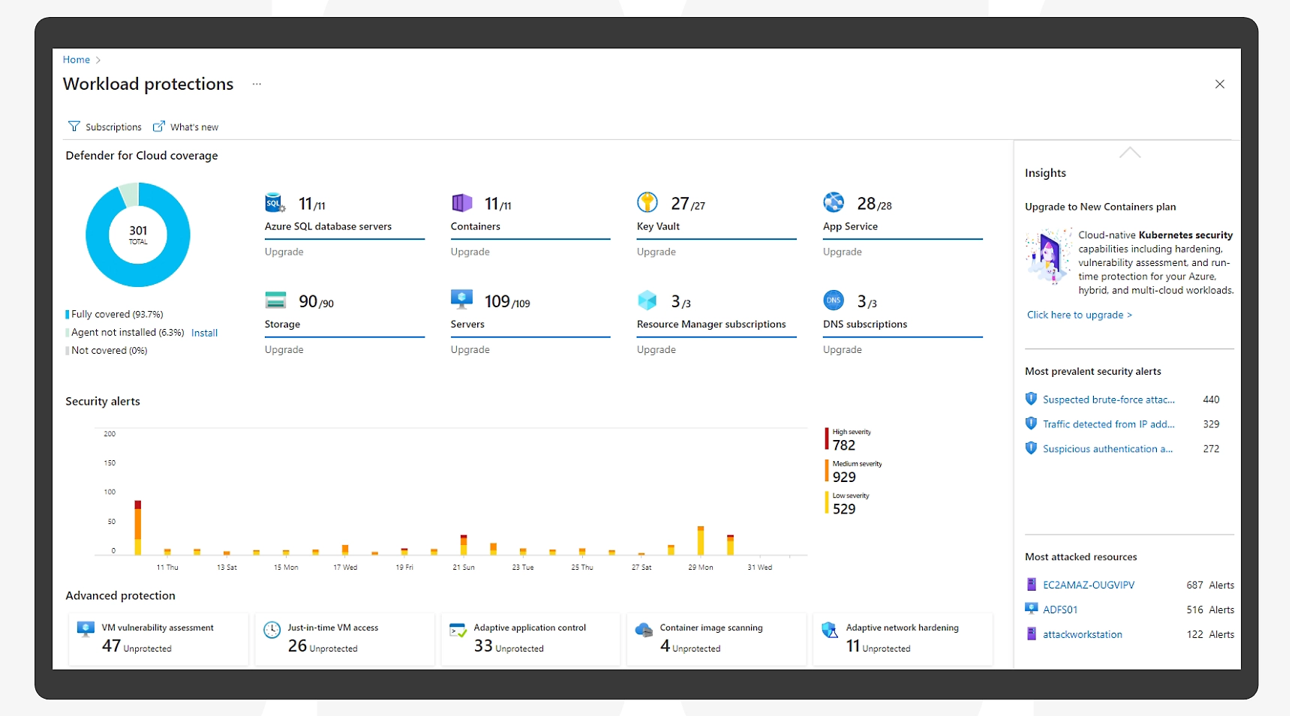
CWPP provides real-time protection for your Azure workloads from malware, ransomware, and other threats. It protects your virtual machines, containers, and web apps from various types of attacks.
Threat Protection
Microsoft Defender for Cloud monitors your Azure resources for threats and provides alerts and recommendations to help you protect your resources from malicious activity.
Incident Response
In the event of a security incident, Microsoft Defender for Cloud helps you investigate and respond to the incident quickly and effectively. It provides tools and guidance to help you mitigate the impact of the incident and prevent future occurrences.
Compliance with Security Regulations
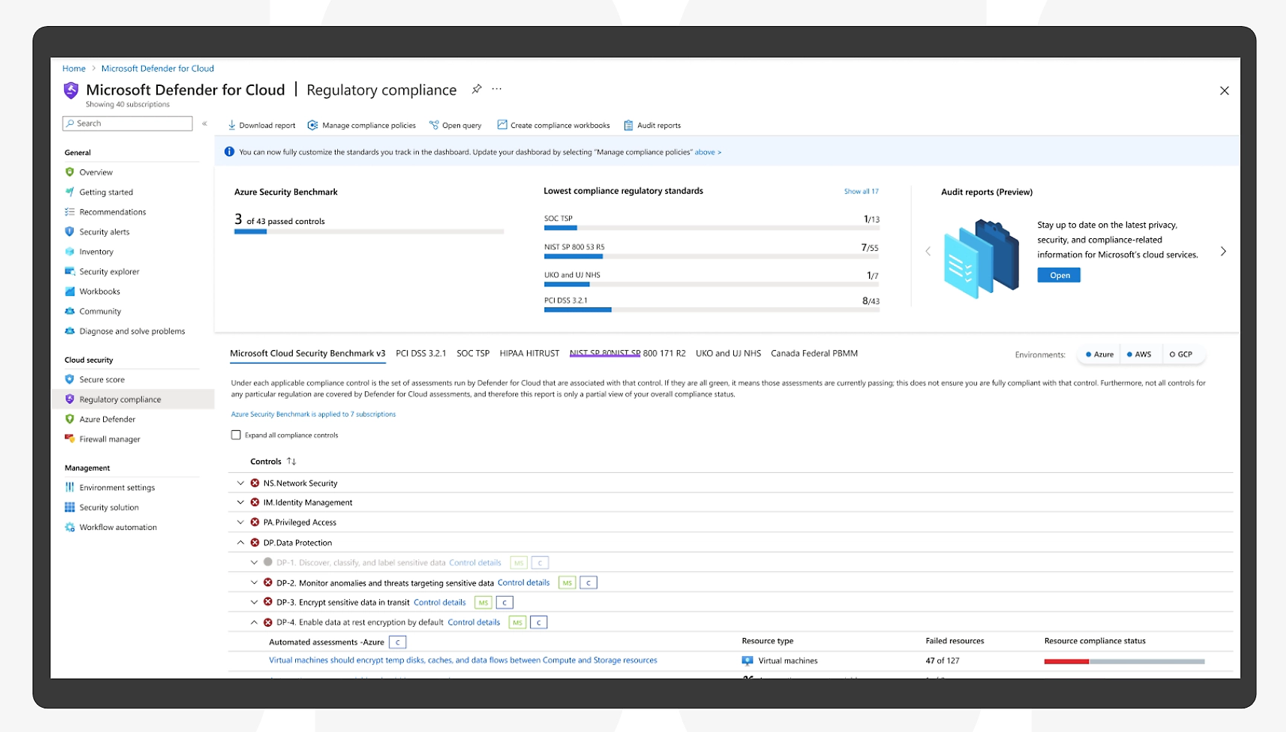
Microsoft Defender for Cloud can help organizations comply with security regulations, such as:
- PCI DSS
- HIPAA
- GDPR
- SOC 2
- ISO 27001
Regulatory compliance is the process of ensuring that an organization’s information security practices meet the requirements of a specific regulation. Regulations are typically issued by government agencies or industry bodies and are designed to protect sensitive data and prevent unauthorized access, use, disclosure, modification, or destruction of data.
Compliance can be a complex and challenging process, but it is essential for organizations that collect, store, or process sensitive data. Microsoft Defender for Cloud helps organizations comply with security regulations by identifying and remediating security misconfigurations, protecting Azure workloads from threats, providing alerts and recommendations, and automating security tasks.
Attack Path Analysis
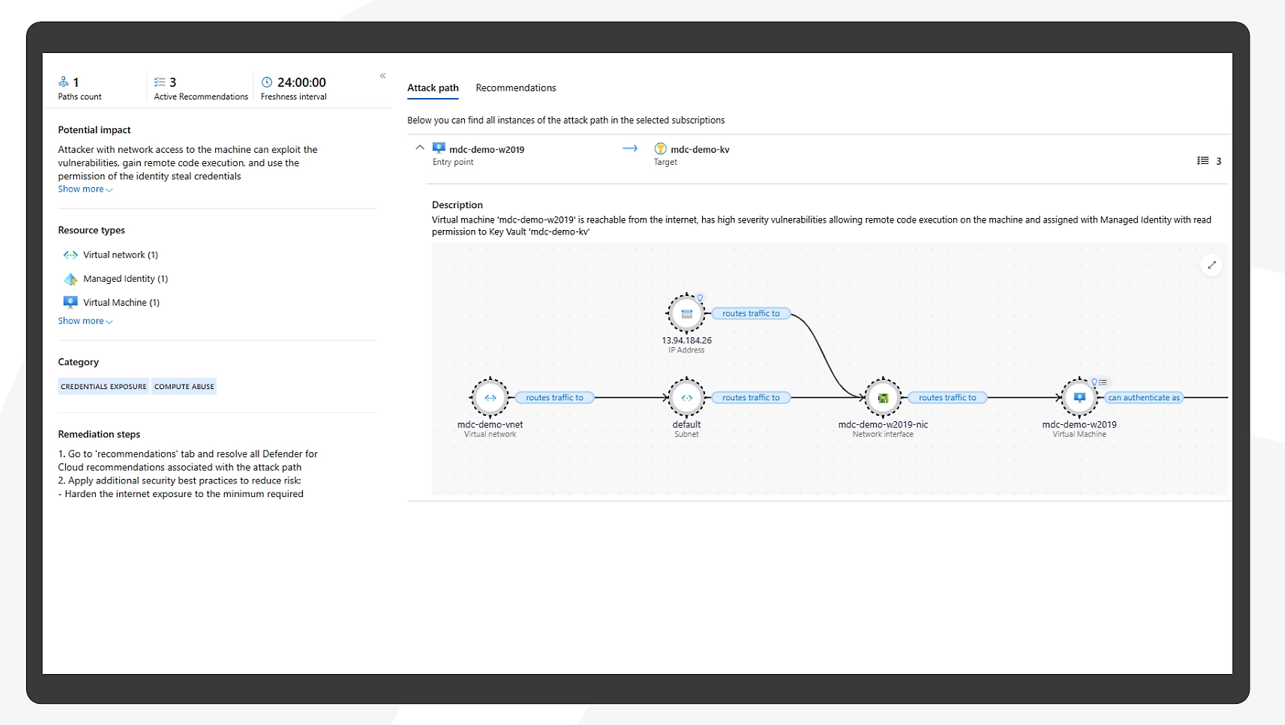
Attack path analysis is a security analysis technique that identifies and assesses the potential attack paths that an attacker could use to compromise an organization’s systems and data.
Microsoft Defender for Cloud provides attack path analysis by:
- Providing a comprehensive view of an organization’s Azure resources
- Identifying potential attack paths and vulnerabilities
- Providing recommendations for mitigating risks
- Automating security tasks, such as scanning for misconfigurations and blocking threats
Enhancing Cloud Security with Microsoft Defender for Cloud
Microsoft Defender for Cloud allows you to:
- Improve your security posture and reduce your risk of being attacked.
- Protect your Azure workloads from malware, ransomware, and other threats.
- Detect and respond to threats quickly and efficiently.
- Comply with security regulations.
Conclusion
In conclusion, Microsoft Defender for Cloud is a powerful tool that helps you enhance the security of your Azure resources. By leveraging its comprehensive set of features, you can better protect your data, applications, and infrastructure in the cloud. Whether it’s identifying security misconfigurations, protecting against malware, or responding to security incidents, Microsoft Defender for Cloud has you covered. So, why wait? Start securing your cloud environment today with Microsoft Defender for Cloud!
Further Exploration
References:
- Create an Azure Account Now!
- Learn More About Azure!
- Microsoft Defender for Cloud Overview
- MITRE Attack Tactics
If you have any questions or wish to explore specific topics further, feel free to reach out to me:
- Bryan Anthony Garcia
- @mindofai
- bryananthonygarcia@live.com
Thank you for reading!